Link-Security™ Software
for Napatech F2070X Infrastructure Processing Unit (IPU)
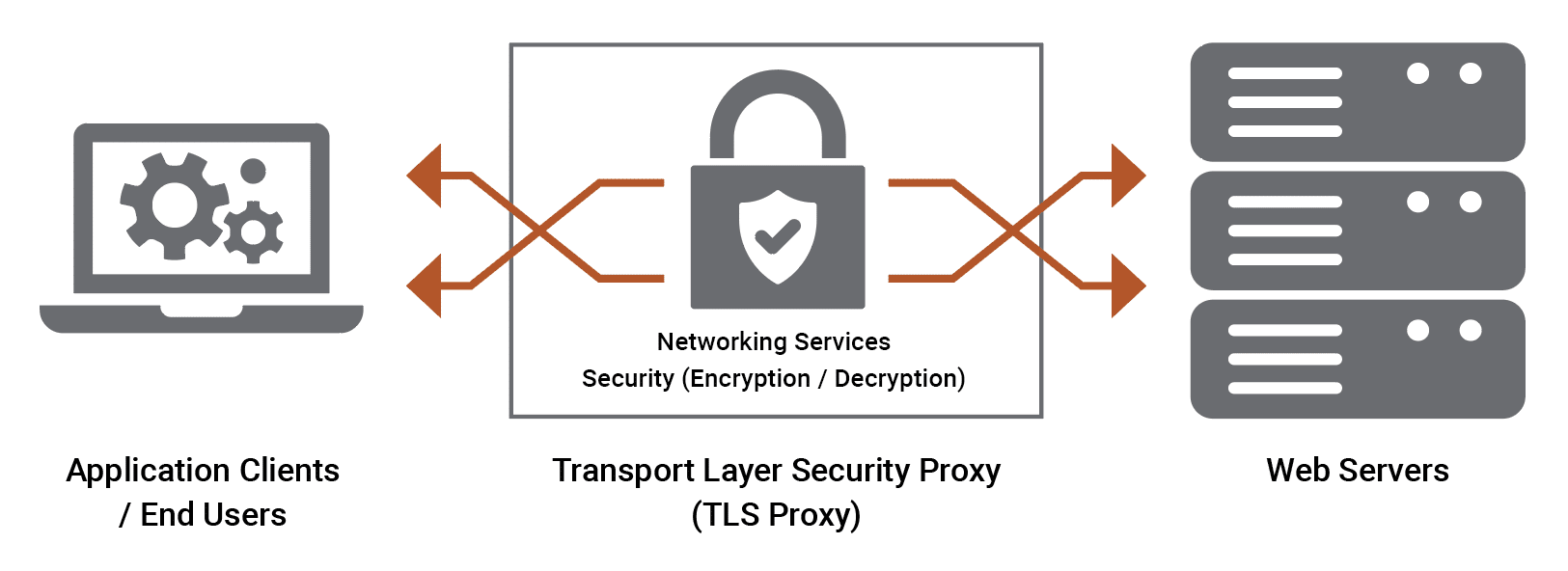
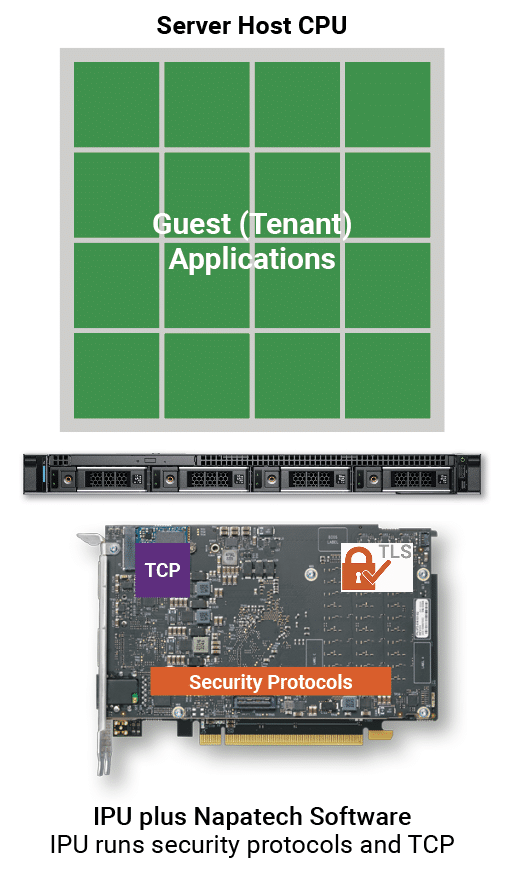
Napatech’s integrated hardware-plus-software solution, comprising the Link-Security™ software stack running on the F2070X IPU, addresses this problem by offloading the TLS protocol from the host CPU to an IPU while maintaining full software compatibility at the application level.
Napatech’s security offload solution not only frees up host CPU cores which would otherwise be consumed by security protocols but also delivers significantly higher performance than a software-based implementation. This significantly reduces data center CAPEX, OPEX and energy consumption.
The Napatech solution also introduces a security layer into the system, isolating system-level infrastructure processing from applications and revenue-producing workloads. This increases protection against cyber-attacks, which reduces the likelihood of the data center suffering security breaches and high-value customer data being compromised, while allowing customers full control of host system resources.
Key Benefits
Napatech provides the unique combination of the industries highest performance F2070X IPU with software to offload and accelerate data center networking services.
Resource Optimization
Offloading the TLS protocol to an IPU frees up valuable CPU resources that can be used for guest (tenant) applications.
Performance
IPUs are optimized to execute TLS encryption and decryption operations faster than general-purpose CPUs. Offloading TLS to an IPU leads to significant performance improvements, especially in scenarios where TLS processing is a bottleneck and/or there’s a need to process a large volume of encrypted data.
Parallel Processing
IPUs are designed for parallelism, allowing them to execute multiple tasks simultaneously. TLS operations involve mathematical computations that can be parallelized, enabling faster execution and more efficient resource utilization.
Scalability
As traffic increases, IPUs can be scaled by adding more units to the infrastructure. This scalability helps maintain consistent TLS performance levels even when dealing with higher loads.
Low Latency
IPUs can reduce the latency associated with TLS encryption and decryption. This is especially important for applications that require real-time communication, minimizing delays in data transfer.
Energy Efficiency
Offloading TLS to an IPU and freeing up host CPU resources for guest applications can reduce the total number of servers required in a data center, resulting in energy savings and reduced OPEX.
Security Enhancements
Many IPUs include hardware-based, zero-root-of-trust security features that enhance the security of TLS operations. These features provide additional protection against certain types of attacks and vulnerabilities.
Simplified Software Stack
By offloading TLS operations to an IPU, the main CPU’s software stack can be simplified, resulting in easier management and maintenance of the system. This can also lead to reduced security vulnerabilities.
Future-Proofing
IPUs can be designed or updated in software to support new TLS encryption standards and algorithms as they emerge. This ensures that the data center infrastructure remains secure and compatible with evolving security requirements.
Key Features
Napatech Link-Security™ Software provides the Napatech F2070X IPU with a robust feature set and extendable architecture allowing configurable, offload and accelerate data center networking services.
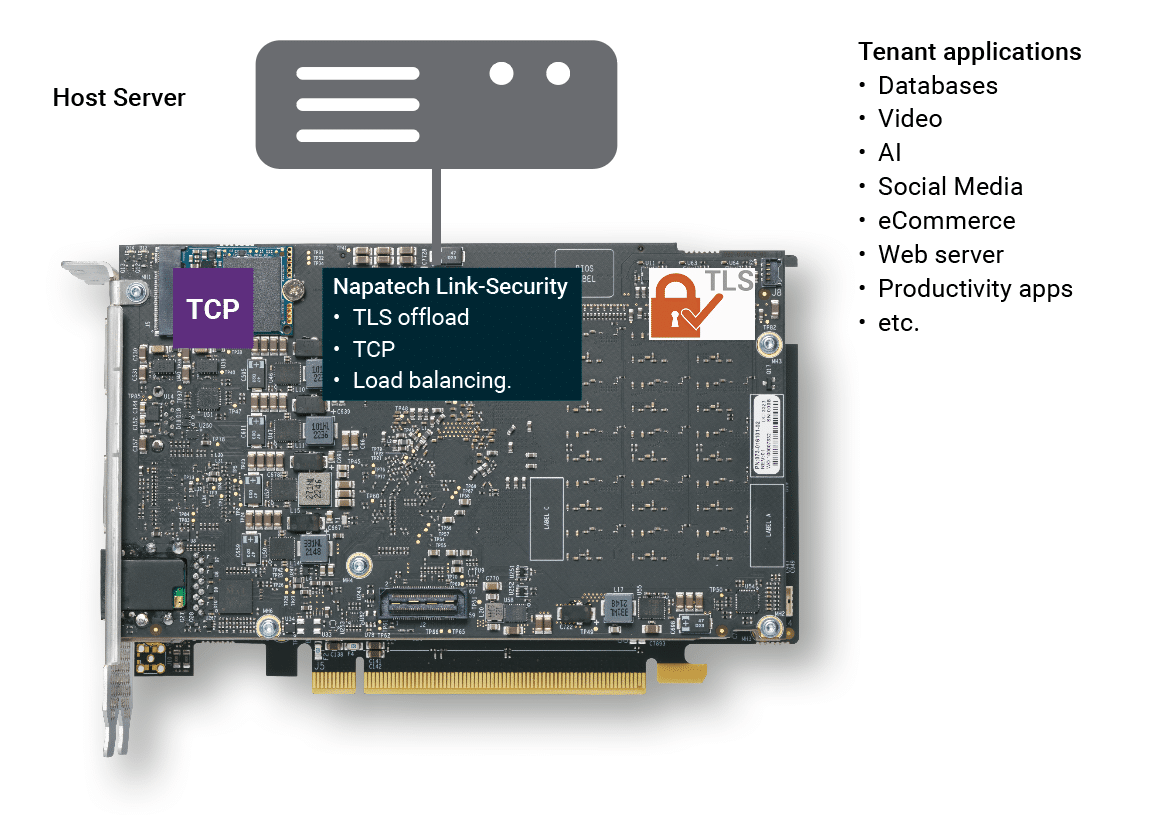
Full offload of TLS encryption and decryption
TCP processing
Load balancing to host CPUs
Web server acceleration
Distributed Denial of Service (DDoS)
Legacy applications without TLS security
Security isolation layer between the host CPU and the IPU
TLS: the standard security protocol for communications between web applications and servers
Transport Layer Security (TLS) is a cryptographic protocol that provides end-to-end security for data sent between applications over the internet. It is mostly familiar to users through its use in secure web browsing, and in particular the padlock icon that appears in web browsers when a secure session is established. However, it is also be used for other applications such as e-mail, file transfers, video/audio conferencing, instant messaging and Voice-over-IP (VoIP). TLS evolved from Secure Socket Layers (SSL) which was originally developed to secure web sessions. The first version of the protocol was released in 1999 and the most recent version is TLS 1.3, which was published in 2018.
TLS is used in data centers to ensure confidentiality, authentication and data integrity. It provides a secure communication channel between servers over the data center network, ensuring that the data exchanged between them remains private and tamper-proof. Key benefits include:
- Data Encryption: One of the primary reasons for using TLS in data centers is to encrypt the data being transmitted between servers and clients within the data center. This encryption ensures that even if the data is intercepted by malicious actors, they won’t be able to understand or decipher the actual content of the data. In a multi-tenant environment, where multiple tenants are using the same data center resources, TLS ensures that data belonging to one client remains private and inaccessible to others.
- Data Integrity: TLS provides mechanisms to ensure that the data being transmitted has not been altered or tampered with during transmission. This is achieved through techniques like Message Authentication Codes (MACs) and hash functions. Using TLS for internal communication ensures that even if a part of the infrastructure is compromised, the data exchanged between components remains protected.
- Authentication: TLS enables authentication of the parties involved in communication. This means that the client and server can verify each other’s identity, ensuring that data is exchanged only with trusted entities. This is critical in a data center environment to prevent unauthorized access and data breaches.
- Protection Against Man-in-the-Middle Attacks: TLS helps protect against man-in-the-middle attacks, whereby an attacker intercepts and potentially modifies the communication between two parties without their knowledge. By encrypting the data and using digital certificates for authentication, TLS mitigates the risk of such attacks.
- Compliance and Regulatory Requirements: Many industries and regions have specific regulations and compliance requirements related to data security and privacy. Implementing TLS helps data centers adhere to these regulations by ensuring the confidentiality and integrity of the data they handle.
- Secure Management Interfaces: Data centers often have management interfaces and APIs that allow administrators to control and monitor various aspects of the infrastructure remotely. Securing these interfaces with TLS prevents unauthorized access and manipulation of critical systems.
- Securing Cloud Services: Many modern data centers provide cloud services and TLS is essential for securing communication between users and the cloud infrastructure, as well as communication between different cloud services.
In summary, TLS is critical to modern data centers because it provides a comprehensive layer of security, protecting the confidentiality, integrity and authenticity of data as it is transmitted and communicated within the data center environment.
IPU-based security offload
Offloading the TLS protocol to an Infrastructure Processing Unit (IPU) which also runs services such as Transmission Control Protocol (TCP), addresses the limitations of a software-only implementation and delivers significant benefits to data center operators:
- Resource Optimization: Offloading the TLS protocol to an IPU frees up valuable CPU resources that can be used for guest (tenant) applications.
- Performance: IPUs are optimized to execute TLS encryption and decryption operations faster than general-purpose CPUs. Offloading TLS to an IPU leads to significant performance improvements, especially in scenarios where TLS processing is a bottleneck and/or there’s a need to process a large volume of encrypted data.
- Parallel Processing: IPUs are designed for parallelism, allowing them to execute multiple tasks simultaneously. TLS operations involve mathematical computations that can be parallelized, enabling faster execution and more efficient resource utilization.
- Scalability: As traffic increases, IPUs can be scaled by adding more units to the infrastructure. This scalability helps maintain consistent TLS performance levels even when dealing with higher loads.
- Low Latency: IPUs can reduce the latency associated with TLS encryption and decryption. This is especially important for applications that require real-time communication, minimizing delays in data transfer.
- Energy Efficiency: Offloading TLS to an IPU and freeing up host CPU resources for guest applications can reduce the total number of servers required in a data center, resulting in energy savings and reduced OPEX.
- Security Enhancements: Many IPUs include hardware-based, zero-root-of-trust security features that enhance the security of TLS operations. These features provide additional protection against certain types of attacks and vulnerabilities.
- Simplified Software Stack: By offloading TLS operations to an IPU, the main CPU’s software stack can be simplified, resulting in easier management and maintenance of the system. This can also lead to reduced security vulnerabilities.
- Future-Proofing: IPUs can be designed or updated in software to support new TLS encryption standards and algorithms as they emerge. This ensures that the data center infrastructure remains secure and compatible with evolving security requirements.
In addition to the above benefits that apply to the TLS workload, the IPU-based system architecture also introduces a security layer into the system, isolating system-level infrastructure processing from applications and revenue-producing workloads. This ensures that the TLS and TCP functions cannot be compromised by a cyber-attack launched by a tenant application. The infrastructure services themselves are secured since the boot process of the IPU itself is secure, while the IPU then acts as the root of trust for the host server.
Napatech security offload solution
Napatech provides an integrated, system-level solution for data center security offload, comprising the high-performance Link-Security™ software stack running on the F2070X IPU.
The Link-Security software incorporates a rich set of functions, including:
- Full offload of TLS encryption and decryption from the host to the IPU;
- TCP processing, including TCP Checksum Offloading (TSO), Generic Receive Offload (GRO), Generic Segmentation Offload (GSO), Large Receive Offload (LRO) and checksumming;
- Load balancing to host CPUs;
- Web server acceleration (reduced page load time) with static file caching and image optimization;
- Enhanced security including Distributed Denial of Service (DDoS) mitigation and malicious traffic filtering;
- For legacy applications without TLS security, the IPU with reverse proxy adds TLS encryption layer on top of clear-text communications;
- Security isolation layer between the host CPU and the IPU, with no network connectivity exposed to the host.
Since the F2070X is based on an FPGA and CPU rather than ASICs, the complete functionality of the platform can be updated after deployment, whether to modify an existing service, to add new functions or to fine-tune specific performance parameters. This reprogramming can be performed purely as a software upgrade within the existing server environment, with no need to disconnect, remove or replace any hardware.
Compatible Napatech F2070X IPU
The Link-Security™ Software is available for Napatech F2070X IPU.
F2070X Infrastructure Processing Unit (IPU)
2x100G
The Napatech F2070X Infrastructure Processing Unit (IPU) is a 2x100Gbe PCIe card with an Intel Agilex® AGFC023 FPGA and an Intel® Xeon® D SoC. The unique combination of FPGA and full-fledged Xeon CPU on a PCI card allows for unique offload capabilities.
These IPUs offer flexibility to create high-performance solutions in server platforms for supporting network infrastructures up to 100G and can be reconfigured to support specific IPU functionality. They are available in both a self-contained cooling and passive cooling version.
Tech specs
| FEATURES | Link-Security™ Software for Napatech F2070X IPU |
| Application Stack Acceleration Framework (ASAF) |
|
| Security Offload |
|
| Supported Hardware and Transceivers |
|