As Communications Service Providers (CSPs) worldwide scale up the deployments of their 5G networks, they face strong pressure to optimize their Return on Investment (RoI), given the massive expenses they already incurred to acquire spectrum as well as the ongoing costs of infrastructure rollouts.
Analytics in full flow
Flow records for advanced flow analytics
In my blog Packet Capture – the Complete Source to the Truth, I explained why network packets are the ultimate source for reliable network analysis. But as network speeds continue to grow and the number of network packets persistently rocket, it is no longer a viable solution to do “live” analysis and DPI on a packet-by-packet basis.
As a consequence, a lot of network monitoring and analysis tools focus on flow records, which they collect from NetFlow/IPFIX probes in the network. Based on these flow records, they are able to detect strange behavior and anomalies that need further analysis. Whenever an incident is detected, it is still possible to go even deeper and analyze the underlying network packets if needed.
Typical use
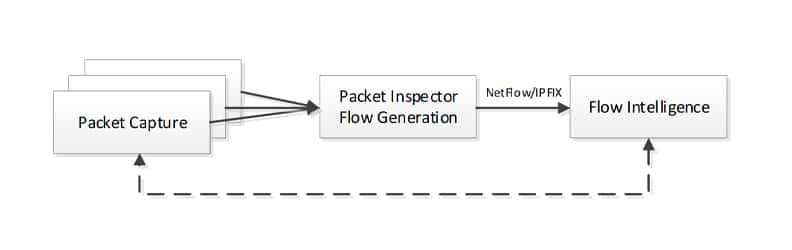
Many of the most advanced network security products available today are implemented this way. They involve both packet capture and packet inspection, including DPI, that result in NetFlow records with metadata. The flows are generated and forwarded to some type of flow-aware intelligence doing more advanced analytics, typically using Artificial Intelligence and machine learning for detection of anomalies and other security issues. Whenever an issue is detected, the flow intelligence has the option to go back and retrieve the underlying packet from the packet capture device for further inspection and analysis.
The figure below shows an example of such a configuration and the same setup is used with or without the packet capture, depending on the need for detailed analysis and documentation of incidents.
Any of the blocks in such a setup can be accelerated by a SmartNIC. For packet capture, the SmartNIC can guarantee zero packet loss and exact timestamping of packets and metadata to improve and accelerate packet indexing. It can even help in forwarding the timestamp or other metadata to the Packet Inspector. For packet inspection, the SmartNICs can extract any forwarded metadata from the packet capture block and help by doing some level of packet decoding; it could also include look-aside acceleration for things like decryption and/or RegEx searches. For the Flow Intelligence, the acceleration needed is more in the area of Machine Learning or Artificial Intelligence but these tasks can also be accelerated using SmartNICs with look-aside engines.
The future: AI on a SmartNIC
In the future, it may even be necessary to accelerate the flow processing by letting the flow/intelligence/anomaly detection happen on the SmartNIC as well. This will require that the SmartNIC includes an AI inference engine capable of executing the Machine Learning model specified by the user and used to detect anomalies or strange behavior.
At Napatech, we have now added flow metrics and state collection to our flow management capabilities, enabling applications to generate NetFlow and IPFIX records with a very limited CPU load, even at full 2×100 Gbps network speed. To demonstrate this, we have implemented a basic IPFIX probe that runs at full 2×100 Gbps, as demonstrated in the video below.
This will enable and accelerate high speed NetFlow/IPFIX probes significantly as most of the packet processing is done in the SmartNIC and only the learning of the flow and the generation of the NetFlow/IPFIX record are done in the CPU. This solution will be available on our newest generation of SmartNICs that support any network speed, e.g.: 8×10 Gbps, 4×25 Gbps, 2×40 Gbps and 2×100 Gbps on the same hardware platform.
The SmartNIC gets even smarter
Going forward, we are investigating the possibility of adding an AI inference engine to our SmartNICs which will be able to accelerate the flow analysis even further and actually detect anomalies in the SmartNIC, based on a machine learning model that is attained elsewhere and executed directly in the SmartNIC.